
In the world of business travel, preparation is everything. From visa requirements and flight schedules to entry rules and vaccination cards, travelers have learned to navigate a checklist of international travel demands. But one area that continues to fly under the radar—with serious implications—is the inspection of electronic devices at U.S. borders.
Whether you’re an HR leader supporting global mobility or a business traveler carrying sensitive company data across borders, understanding how these searches work is no longer optional.
The legal landscape: CBP’s expansive authority.
Under U.S. law, U.S. Customs and Border Protection (CBP) has broad authority to inspect the belongings of anyone entering the country. This includes the power to search electronic devices like laptops, smartphones, tablets, and USB drives—sometimes without a warrant, and even without suspicion.
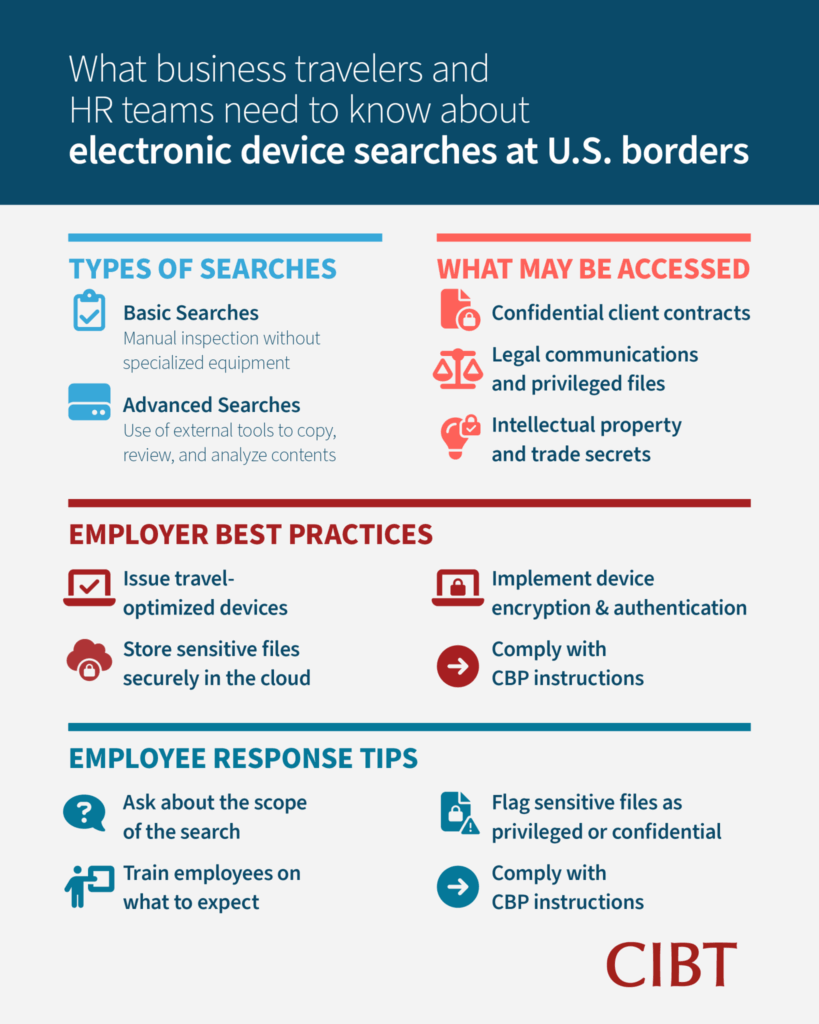
CBP categorizes searches into two types:
Basic Searches: CBP officers manually inspect your device without any specialized equipment.
Advanced Searches: Devices are connected to external tools that can copy, review, and analyze contents, including deleted files and encrypted materials.
Both types of searches are legal, and neither requires a warrant, probable cause, or even reasonable suspicion. This expansive authority has been upheld by U.S. courts under the “border search exception,” a doctrine that gives the government more leeway at borders than it would have inland.
CBP’s enforcement practices around electronic device inspections change frequently—often without formal notice—so it’s important for employers and travelers to stay up to date.
Implications for business travelers and corporate stakeholders.
Electronic device inspections are a routine part of international travel and may involve the examination of laptops, phones, or other work-issued equipment. Many employees—particularly those in executive, sales, consulting, or technical roles—travel with devices that support critical business functions. Establishing clear protocols for managing this data during cross-border travel helps ensure continuity, security, and compliance.
Types of information that may be accessed during a device inspection include:
- Confidential client contracts
- Legal communications and privileged files
- Intellectual property and trade secrets
- Financial documents and internal strategy materials
In the event of a search or seizure, this content may be viewed, copied, or retained. Even deleted or encrypted data may be accessed in an advanced search. For companies with cross-border operations, this exposure poses legal, reputational, and regulatory risks—especially in industries with strict data security requirements.
How companies can support secure and compliant travel.
Proactive preparation helps ensure that international business travel proceeds smoothly and in alignment with company policies. Employers can support travelers by implementing clear protocols, training, and technology practices. The following measures are commonly used by companies managing cross-border travel or global mobility programs:
1. Issue travel-optimized devices.
Assign laptops or phones configured specifically for international travel. These devices should provide access to the necessary tools and information without storing large volumes of sensitive data locally. This approach supports data security, regulatory compliance, and a smoother inspection process when required.
2. Store sensitive files in secure cloud environments.
Encourage employees to access critical documents through encrypted, cloud-based platforms rather than saving files directly to their device. Access can be limited by time or location.
3. Implement device encryption and authentication.
Ensure all travel devices are encrypted and protected by strong passwords, biometric security, or multi-factor authentication. Devices should be shut down (not just in sleep mode) before border inspection to require re-entry of credentials.
4. Train employees on what to expect.
Employees should be made aware of CBP’s authority to inspect electronic devices and how to respond if stopped, including what information they are legally required to provide and when they may request clarification or flag sensitive content.
5. Establish a response protocol.
If a device is searched or seized, the company’s IT, legal, and HR teams should be notified immediately. Internal protocols should include chain-of-custody tracking, breach response procedures, and communications guidance.
What employers should avoid.
In addition to proactive strategies, companies should be aware of common missteps that increase risk during device inspections:
1. Avoid storing privileged or confidential files locally.
Even encrypted documents may be accessed or copied during an inspection. Privileged or sensitive materials should be hosted securely off-device and accessed only through cloud-based platforms.
2. Avoid assuming inspections apply only to foreign nationals.
Device search authority applies to all travelers. U.S. citizens may still have devices searched or confiscated, even though they cannot be denied entry.
3. Avoid instructing employees to refuse all requests.
Refusing to provide access or passwords may be legally permissible, but it can result in device seizure or travel disruption. Employees should be trained to respond in accordance with company policy—not act on impulse.
4. Avoid letting travelers decide what’s sensitive.
Companies should not rely on employees to self-determine what files should or shouldn’t be stored on their devices. Pre-trip preparation and clear device policies help ensure alignment with data protection goals.
Common questions from HR and legal teams.
Can employees refuse a search?
Yes, but refusal may result in device confiscation and, for non-U.S. citizens, denial of entry. U.S. citizens cannot be refused entry but may still face retention of devices.
How long can CBP keep a device?
There is no statutory limit. Most devices are returned within 5-15 days, but longer retention periods are possible.
What if the device contains attorney-client privileged information?
Travelers may assert privilege and request that CBP follow specific procedures for handling such materials. However, the assertion of privilege does not guarantee immunity from inspection.
Does this apply only to business travelers?
No. All travelers entering the U.S.—including tourists, students, and permanent residents—may be subject to these inspections. However, business travelers are more likely to carry sensitive data that warrants additional precautions.
What happens if a device is searched?
If stopped by CBP, travelers should remain calm and professional. Here’s what to keep in mind:
You can ask questions: Inquire about the scope of the search and whether it’s basic or advanced.
You can assert privilege: If files contain attorney-client communications or trade secrets, clearly identify them as privileged or confidential.
You can request documentation: If your device is confiscated, request a receipt and details about how long the device may be held.
You must comply: Declining to provide a password may lead to CBP retaining the device and denying entry (for non-U.S. citizens).
It’s also important to report the incident immediately to your HR or legal department for review and potential action.
Why this matters more now than ever.
Global business travel is recovering, but it’s not business as usual. As companies expand international operations, the movement of people and information is increasingly intertwined.
Risk mitigation was also a key theme at the GBTA Canada Conference 2025, where mobility leaders discussed the increasing complexity of cross-border travel and the importance of compliance at every stage.
Every trip, client meeting, and cross-border collaboration now comes with digital footprints and digital vulnerabilities. CBP recorded over 45,000 electronic device searches in a single fiscal year, and the number continues to rise.
At the same time, the digital transformation of work means mobile professionals are carrying more sensitive information across borders than ever before. From intellectual property to client data, one unexpected search could expose critical company assets—whether or not anything was done wrong.
This is not just an IT issue. It’s a business risk, and one that requires proactive planning.
Conclusion: A proactive approach is your best defense
The bottom line is this: Border searches are real. They are increasing. And they are legal.
Whether you’re an HR leader managing outbound assignments or a traveler flying in for a sales pitch, knowing your rights and preparing for the risks of electronic device searches should be standard practice—not an afterthought.
Creating smart travel policies, training employees, and minimizing the amount of sensitive data carried across borders are essential steps toward reducing risk and protecting your business.
Need support on managing electronic device searches at U.S. borders?
Newland Chase helps companies and global travelers navigate complex immigration scenarios, including cross-border business travel, visa compliance, and digital security considerations during international trips.
To learn more or to discuss how we can help you develop secure, compliant mobility practices, please contact us today.
This article is intended for informational purposes only and is not a substitute for legal advice. Immigration law and enforcement practices are subject to change. For case-specific guidance, consult an attorney or speak with a Newland Chase advisor.
